[THM] Phishing Emails 3 by TryHackMe
Great Work Getting Here!
I've got a few more posts to slam on out so I'm going to jump right on into this one.
Task 1
Q: Read the above.
A: No answer needed
Task 2
Q: Read the above.A: No answer needed
Task 3
Q: What is the official site name of the bank that capitai-one.com tried to resemble?A: capitalone.com
Task 4
Q: How can you manually get the location of a hyperlink?A: Copy link location
Task 5
Q: Read the above.A: No answer needed
Task 6
Q: Look at the Strings output. What is the name of the EXE file?A: *See below*
Check out the screenshots in the module for the answer.
Task 7
Q: What brand was this email tailored to impersonate?A: Netflix
Q: What is the From email address?
A: JGQ47wazXe1xYVBrkeDg-JOg7ODDQwWdR@JOg7ODDQwWdR-yVkCaBkTNp.gogolecloud.com
Use your header analysis tools!
Q: What is the originating IP? Defang the IP address.
A: *defang this thing!*
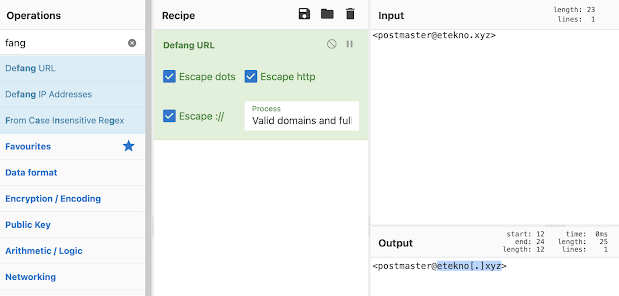
Q: From what you can gather, what do you think will be a domain of interest? Defang the domain.
A: etekno[.]xyz
Q: What is the shortened URL? Defang the URL.
A: hxxps[://]t[.]co/yuxfZm8KPg?amp=3D
It is without the last =!!
Task 8
Q: What is this analysis classified as?
A: Suspicious activity
Tip here - Select text report and a few answers are there at the top of the page.
Q: What is the name of the PDF file?
A: Payment-updateid.pdf
See screenshot on question above!
Q: What is the SHA 256 hash for the PDF file?
A: CC6F1A04B10BCB168AEEC8D870B97BD7C20FC161E8310B5BCE1AF8ED420E2C24
See screenshot on question above!
Q: What two IP addresses are classified as malicious? Defang the IP addresses. (answer: IP_ADDR,IP_ADDR)
A: 2[.]16[.]107[.]24, 2[.]16[.]107[.]83
Continue looking at your text report to find the Connectors section!
Q: What Windows process was flagged as Potentially Bad Traffic?
A: svchost.exe
Task 9
Q: What is this analysis classified as?
A: Malicious activity
Open the text report to save some time.
Q: What is the name of the Excel file?
A: CBJ200620039539.xlsx
Q: What is the SHA 256 hash for the file?
A: 5F94A66E0CE78D17AFC2DD27FC17B44B3FFC13AC5F42D3AD6A5DCFB36715F3EB
Q: What domains are listed as malicious? Defang the URLs & submit answers in alphabetical order. (answer: URL1,URL2,URL3)
A: biz9holdings[.]com,findresults[.]site,ww38[.]findresults[.]site
Q: What IP addresses are listed as malicious? Defang the IP addresses & submit answers from lowest to highest. (answer: IP1,IP2,IP3)
A: 204[.]11[.]56[.]48,103[.]224[.]182[.]251,75[.]2[.]11[.]242
Q: What vulnerability does this malicious attachment attempt to exploit?
A: CVE-2017-11882
Task 10
Q: Read the above.A: No answer needed